July 24, 2020
- How To Phishing Facebook
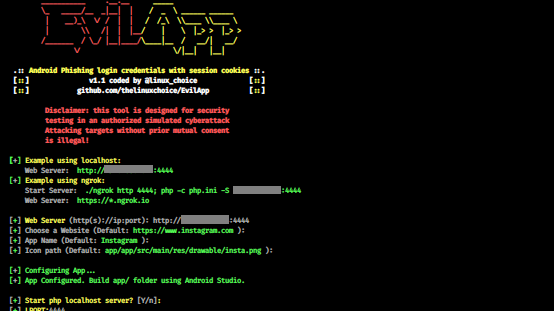
- How To Do Phishing Using Android Without
- How To Make Phishing Site
- How To Do Phishing Using Android Studio
First make a note of the phone number the spam text came from. You'll need it later. To Forward the spam message, tap on the Menu button of your Android and then tap Forward 3. Phishing is the attempt to get the personal information such as username, password etc by using a fake page! They send out e-mails that appears to come from the legitimate websites such as e-bay,Paypal etc and when you click those links they ask you to enter your details such as password, e-mail, Credit card number and once you enter your. Scams and phishing attacks are on the rise around the world, and it's easy to fall prey if you're not aware of particular types of attacks. Despite strong security on both iOS and Android, it. If you’ve ever wondered how to hack an Android phone by sending a link – phishing is the answer. So, how does phishing work? Phishing is one of the most popular ways to hack a phone because it doesn’t require any physical access. The target is contacted via email or SMS.
Save up to $65 on Norton 360 for first year*
Get multiple layers of protection for your Cyber Safety. Don't wait!
Does my Android phone have a virus? Is it infected with malware or a malicious app? Will my personal information be held for ransom? If you find yourself asking these questions, then here is some useful information about Android devices and antivirus apps that may help you.
Viruses and other types of malware
Malware is malicious software that can sneak onto your phone. Written with the intent to cause harm, malware can include viruses, computer worms, Trojans, ransomware, and spyware.
Cybercriminals can use malware to access your personal data and, in some cases, subsequently use that sensitive information to commit identity theft or fraud.
Viruses are a particular type of malware that infiltrate a computer or other device and their programs. A cybercriminal may be able to install a virus on your device without your knowledge or consent. The virus may then be able to insert new, malicious code on your device that can monitor and manipulate your online activity.
What can viruses and other malware do to Android phones?
Malware is designed to generate revenue for cybercriminals.
Malware can steal your information, make your device send SMS messages to premium rate text services, or install adware that forces you to view web pages or download apps.
Info stealers can steal your contact list, your personal information, your location, your passwords, and more.
With the aid of malware, cybercriminals can access your devices and steal your information for their own use or to sell on the dark web.
Hackers also use ransomware to lock devices and encrypt personal data. Then they can demand a ransom payment from the victim in order to regain access to their files.
Signs your Android phone may have a virus or other malware
Phones can be vulnerable to damage externally and internally. While the external damage is usually visible, internal damage is usually hidden from view.
Malware like viruses are known to perform repeated tasks that can take up resources on your devices. Signs of malware may show up in these ways.
- Your phone is too slow.
- Apps take longer to load.
- The battery drains faster than expected.
- There is an abundance of pop-up ads.
- Your phone has apps you don’t remember downloading.
- Unexplained data usage occurs.
- Higher phone bills arrive.
How To Phishing Facebook
How to check for viruses and other malware on your Android phone
A good way to check for malware on your Android phone is to run an antivirus scan.
Before buying antivirus software for your phone, make sure you consider the most comprehensive product that’s available for your device.
There are many antivirus software choices available on the market. Some are free, and some are sold.
It’s a good idea to do your research to ensure the security software you invest in runs a complete scan and doesn’t overlook any vulnerabilities. An incomplete scan could give you a false sense of security when, in fact, your device could be vulnerable to cyberattacks.
Norton Mobile Security for Android is one product you might consider.
How to remove viruses and other malware from your Android device
If you think you have malware on your phone, it’s important to stop the malware from causing any further damage. Here are a few steps you can take.
- Power off the phone and reboot in safe mode. Press the power button to access the Power Off options. Most Android phones come with the option to restart in Safe Mode. Here’s how, according to Google, although Safe Mode can vary by phone: Press your phone's power button. When the animation starts, press and hold your phone's volume down button. Hold it until the animation ends and your phone restarts. You'll see “Safe mode” at the bottom of your screen.
- Uninstall the suspicious app. Find the app in Settings and uninstall or force close it. This may not completely remove the malware, but it could prevent further damage to your device, or from it transmitting the malware to other devices on your network.
- Look for other apps you think may be infected. There’s a chance that some apps may have been infected by the malware. If you think you can identify those apps, delete them immediately.
- Install a robust mobile security app on your phone.
Tips to help protect your Android device against viruses and other malware
Here are seven key steps you can take to help protect against future risks.
- Invest in and use robust security software to protect your Android device.
- Keep all operating systems and software updated with the latest versions.
- Don’t click on suspicious or unfamiliar links in emails and text messages.
- Use strong, complicated passwords or a password manager.
- Never use unsecure Wi-Fi connections. Always use a VPN when connecting to public Wi-Fi.
- Always use strong cyber safety protection on all devices that connect to the internet.
- Always install apps from trusted sources, such as the Google Play Store. Read the fine print and permissions on the apps to understand how much access you are giving the app developers.
It’s a good idea to not wait until your device gets infected. Make protecting your Android device a priority. Having good antivirus software that helps protect your PCs, tablets, and other Android devices could help prevent malware from spreading from device to device.
Save up to $65 on Norton 360 for first year*
Get multiple layers of protection for your Cyber Safety. Don't wait!
How To Do Phishing Using Android Without
Editorial note: Our articles provide educational information for you. NortonLifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about cyber safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses.
Copyright © 2020 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the United States and other countries. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.
'You can fool some of the people all of the time, and all of the people some of the time, but you cannot fool all of the people all of the time.' –Abraham Lincoln
Email phishing examples
SEE ALSO: Fighting Phishing Email Scams: What You Should Know
What is phishing?
This technique is called phishing, and it’s a way hackers con you into providing your personal information or account data. Once your info is obtained, hackers create new user credentials or install malware (such as backdoors) into your system to steal sensitive data.
SEE ALSO: Examples of common phishing attempts.
Phishing emails today rarely begin with, 'Salutations from the son of the deposed Prince of Nigeria...' and it's becoming increasingly difficult to distinguish a fake email from a verified one. But, most have subtle hints of their scammy nature. Here are seven email phishing examples to help you recognize a malicious email and maintain email security.
1. Legit companies don’t request your sensitive information via email
Chances are if you receive an unsolicited email from an institution that provides a link or attachment and asks you to provide sensitive information, it’s a scam. Most companies will not send you an email asking for passwords, credit card information, credit scores, or tax numbers, nor will they send you a link from which you need to login.
| Notice the generic salutation at the beginning, and the unsolicited web link attachment? |

2. Legit companies usually call you by your name
Phishing emails typically use generic salutations such as “Dear valued member,” “Dear account holder,” or “Dear customer.” If a company you deal with required information about your account, the email would call you by name and probably direct you to contact them via phone.
3. Legit companies have domain emails
Don’t just check the name of the person sending you the email. Check their email address by hovering your mouse over the ‘from’ address. Make sure no alterations (like additional numbers or letters) have been made. Check out the difference between these two email addresses as an example of altered emails: michelle@paypal.com michelle@paypal23.com Just remember, this isn’t a foolproof method. Sometimes companies make use of unique or varied domains to send emails, and some smaller companies use third party email providers.| 'Costco's' logo is just a bit off. This is what the Costco logo is supposed to look like. |
| See the difference? Subtle, no? |
4. Legit companies know how to spell
Possibly the easiest way to recognize a scammy email is bad grammar. An email from a legitimate organization should be well written. Little known fact – there’s actually a purpose behind bad syntax. Hackers generally aren’t stupid. They prey on the uneducated believing them to be less observant and thus, easier targets.In addition to the generic salutation, grammar gaffes are usually a good clue that something is wrong. “Please fill this form…” And notice the ‘17’ reference in the middle of the sentence.
5. Legit companies don’t force you to their website
Sometimes phishing emails are coded entirely as a hyperlink. Therefore, clicking accidentally or deliberately anywhere in the email will open a fake web page, or download spam onto your computer.
| This whole email was a gigantic hyperlink, so if you clicked anywhere in the email, you would initiate the malicious attack. |
6. Legit companies don’t send unsolicited attachments
| Just remember, curiosity killed the cat. |
7. Legit company links match legitimate URLs
Just because a link says it’s going to send you to one place, doesn’t mean it’s going to. Double check URLs. If the link in the text isn't identical to the URL displayed as the cursor hovers over the link, that's a sure sign you will be taken to a site you don’t want to visit. If a hyperlink’s URL doesn’t seem correct, or doesn’t match the context of the email, don’t trust it. Ensure additional security by hovering your mouse over embedded links (without clicking!) and ensure the link begins with https://.How To Make Phishing Site
| Although very convincing, the real Nokia wouldn't be sending you a 'Save your stuff' email from info@news.nokia.com |
How To Do Phishing Using Android Studio
David Ellis (GCIH, QSA, PFI, CISSP) is VP of Forensic Investigations at SecurityMetrics with over 25 years of law enforcement and investigative experience.
Join Thousands of Security Professionals and Subscribe
