- Actually, phishing is the way for stealing someone's rare detail like password of any account. In this phishing attack method attackers simply create a clone website of any website like Instagram, Facebook, Gmail, Twitter, etc. In my previous post, I explain the easy method how to hack facebook account?
- I’m often times asked how I perform email email phishing attacks. Email phishing attacks are very compelling, and unique to each situation. The process of creating a successful email phishing campaign is very methodical, and most of the time and effort goes up front into the planning phase.
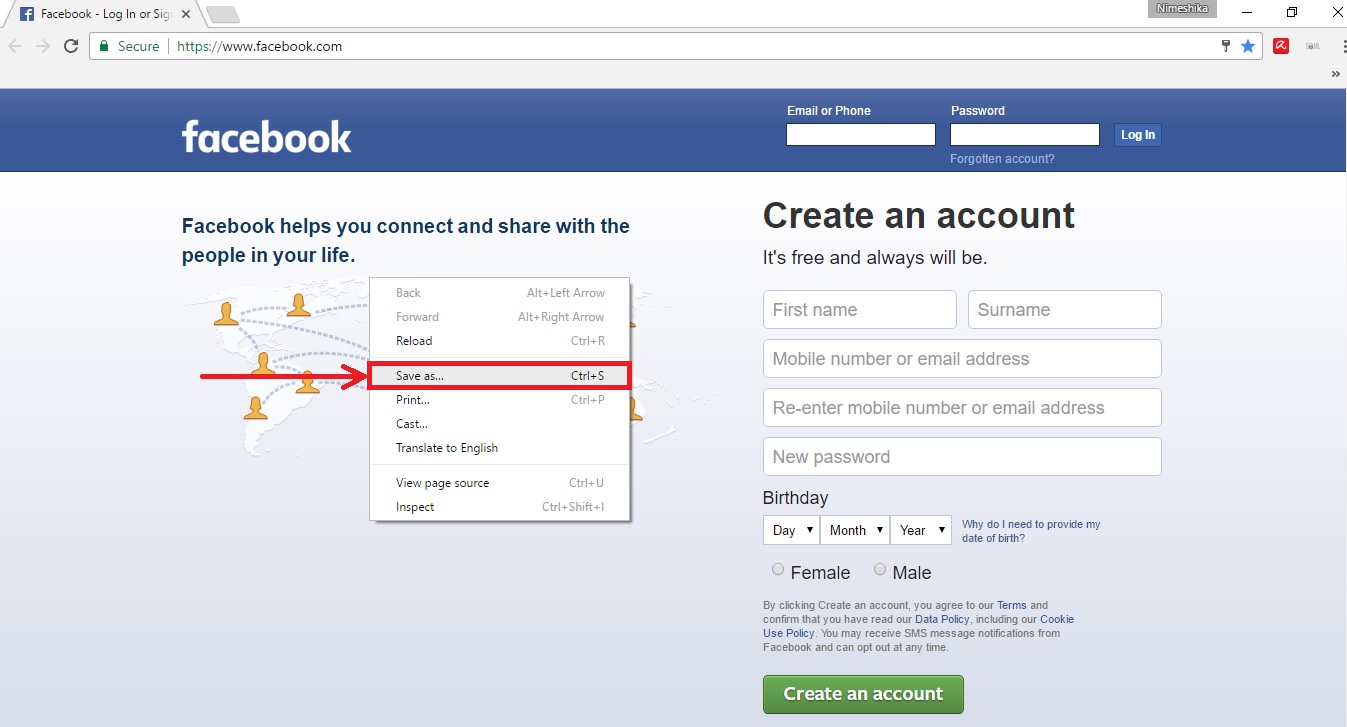
Pull up Facebook.com in your browser. Then, right click on the website’s login page. You should see an option along the. Go ahead and dump all of the page’s source code into Notepad (or your operating system’s best simple text editor). If using Notepad, hit ctrl f (which is the find hotkey). Phishing on social media is a growing problem. It works essentially by users clicking links. For example, you click on a link in a message and then get prompted to sign back into your account - after which your details are stored and your friends.
Phishing attack using kali Linux is a form of a cyber attack which typically relies on email or other electronic communication methods such as text messages and phone calls. It is one of the most popular techniques of social engineering. Where hackers pose as a trustworthy organization or entity and trick users into revealing sensitive and confidential information.
We will create a Facebook phishing page using Social Engineering Toolkit which is a preinstalled functionality in Kali Linux OS. The phishing link can be sent to any user on the same Local Area Network as you and the data that they enter on the fraudulent page will be stored in a file on the attacker’s machine.
Social Engineering Toolkit or SET for short is the standard for social engineering testing among security professionals and even beginners must have a basic idea about using the tool. Basically, it implements a computer-based social engineering attack.
Steps of Phishing Attack:
- Open the terminal window in Kali and make sure you have root access as ‘setoolkit’ needs you to have root access
- Type ‘setoolkit’ in the command line
How To Do Phishing In Facebook Messenger
You will be warned that this tool is to be used only with company authorisation or for educational purposes only and that the terms of service will be violated if you use it for malicious purposes.
- Type y to agree to the conditions and use the tool
- A menu shows up next. Enter 1 as the choice as in this demo we attempt to demonstrate a social engineering attack.
Under Social Engineering, there are various computer-based attacks and SET explains each in one line before asking for a choice.

- Enter 3 which will select the ‘Credential Harvester Attack Method’ as the aim is to obtain user credentials by creating a bogus page which will have certain form fields.
Now, the attacker has a choice to either craft a malicious web page on their own or to just clone an existing trustworthy site.
- Enter 2 in order to select ‘Site Cloner’
This might take a moment as SET creates the cloned page.
- Now you need to see IP address of the attacker machine. Open a new terminal window and write ifconfig
- Copy the IP address stated in ‘inet’ field
- SET will ask you to provide an IP where the credentials captured will be stored. Paste the address that you copied in the earlier step.
- Since we chose to clone a website instead of a personalised one, URL to be cloned is to be provided. In this example, it is www.facebook.com
- Social Engineering Toolkit needs Apache Server running as captured data is written to the root directory of Apache. Enter y when prompted about starting the Apache process.
The set up for a phishing attack is complete, you have cloned Facebook and hosted it on the server. SET informs us the directory at which the captured data will be stored.
The IP address is usually hidden carefully by using URL shortener services to change the URL so that it is better hidden and then sent in urgent sounding emails or text messages.
- Go to browser and type http://yourIP (eg: http://192.168.0.108) Note: I am writing this article from Maharashtra,India hence Facebook is in the native language Marathi.
If an unsuspecting user fills in their details and clicks on ‘Log In’, the fake page takes them to the actual Facebook login page. Usually, people tend to pass it off as a glitch in FB or error in their typing.
- Finally, reap the benefits. Go to /var/www/html and you can see the harvester file created there.
Hope this guide gave you a basic idea of how phishing attacks work.
Phishing is constantly evolving to entrap innocent computer users. Recommended safety tips will be to always check the URL of a website in the browser and use of two-factor authentication as it provides an extra security layer to your account.
How To Do Phishing Attack Facebook
Cybervie provides best cyber security training program in hyderabad, India.This cyber security course enables you to detect vulnerablities of a system, wardoff attacks and manage emergency situations. Taking a proactive approach to security that can help organisations to protect their data, Cybervie has designed its training module based on the cyber security industry requirements with three levels of training in both offensive and defensive manner, and use real time scenarios which can help our students to understand the market up-to its standard certification which is an add on advantage for our students to stand out of competition in an cyber security interview.
More Info – Click Here

Cyber security Course offered by Cybervie prepares students for a path of success in a highly demanding and rapidly growing field of cyber security. The course is completely designed with an adaptable mindset, where the program allows the student to complete the course work at their own pace while being able to complete weekly assignments. Hence, also making it convenient for busy working professionals to pursue the training to help them advance their career in cyber security.
Cybervie has designed the training module based on the cyber security industry requirements in both offensive and defensive manner, using real time scenarios which help our students to understand the market standards.
Interested in Cyber Security Training Program 2020 – Click Here
Here we tells about PHISHING Attacks and How can we protect from it..!!
>>WHAT IS PHISHING:-
The act of sending an e-mail to a user falsely claiming to be an established legitimate enterprise in an attempt to scam the user into surrendering private information that will be used for identity theft. The e-mail directs the user to visit a Web site where they are asked to update personal information, such as passwords and credit card, social security, and bank account numbers, that the legitimate organization already has. The Web site, however, is bogus and set up only to steal the user’s information.
>>MOBILE PHISHING:
Phishing scams are not limited to the internet. Some phishers use the telephone to make requests for information. If you get a call from your banking institution asking for personal information, hang up and call your bank directly. Your bank will have your social security number and account information on file and should only ask you to verify a few digits.
like iPhone, Apple, iTunes and more…By SMS
Example:-
The phisher can ask like it They want your personal Information.
Some people do the reply to phisher then after he/she can be target of Phisher… so never be reply these type of Messages or Mail.
In a phishing attack, the attacker creates a situation wherein people believe that they are dealing with an authorized party, like their bank or another service provider. The attacker will ask the victim for sensitive information such as credit card information.
>>Phishing attacks generally target:
* Bank information – e.g. VISA and PayPal accounts.
* Username and password information.
* Social Security numbers.
* Information which can be used to retrieve forgotten or lost credentials.
>>Follow the tips below to protect yourself against these threats:
- ·Your bank will never ask you to divulge account information or passwords via email. Never give out this information, especially via email.
- Don’t open emails that come from untrusted sources.
- Don’t run files that you receive via email without making sure of their origin.
- Don’t click links in emails. If they come from a known source, type them on the browser’s address bar. If they come from an untrusted source, simply ignore them, as they could take you to a web designed to download malware onto your computer.
- Keep your computer protected. Install a security solution and keep it up-to-date.
>>Protect yourself from Phishing scams that could lead to identity theft. I cannot stress this enough. Phishing scams are a hot topic lately that have grown with the popularity of online banking and social networking sites like MySpace, Facebook and Twitter.
The term Phishing comes from the analogy to “fishing”. The phisher uses a bait to lure victims into giving out personal information like passwords and credit card numbers. The bait is typically and urgent plea from one of the victims friends or trusted websites, asking for information to resolve some sort of problem with their account.
> Anti-phishing software is a must for anyone that accesses the internet. Most of the internet service providers have some safety measures included as part of their online security software. Most web browsers also have add-ons that can detect most phishing scams.
Also read: Protect Yourself With Phishing Protection Software
Unfortunately, these measures are not enough. Some of the more clever phishers have found ways to trick the anti-phishing software so you need to be cautious of suspicious emails and messages.
